Blog
How application containerization can improve data security
There are many different aspects of data security, such as authentication, authorization, encryption, Access Control Lists (ACLs), firewalls, etc., which can be implemented in different ways. Data security is also necessary on many different levels and systems, which can require a range of specific competencies to configure and maintain.
With application containerization, certain data security aspects can be implemented in the container orchestration & management layer (the system that takes care of starting a container image on a machine).
This can help reduce the number of systems needed by using more features of the existing system.
What is application containerization?
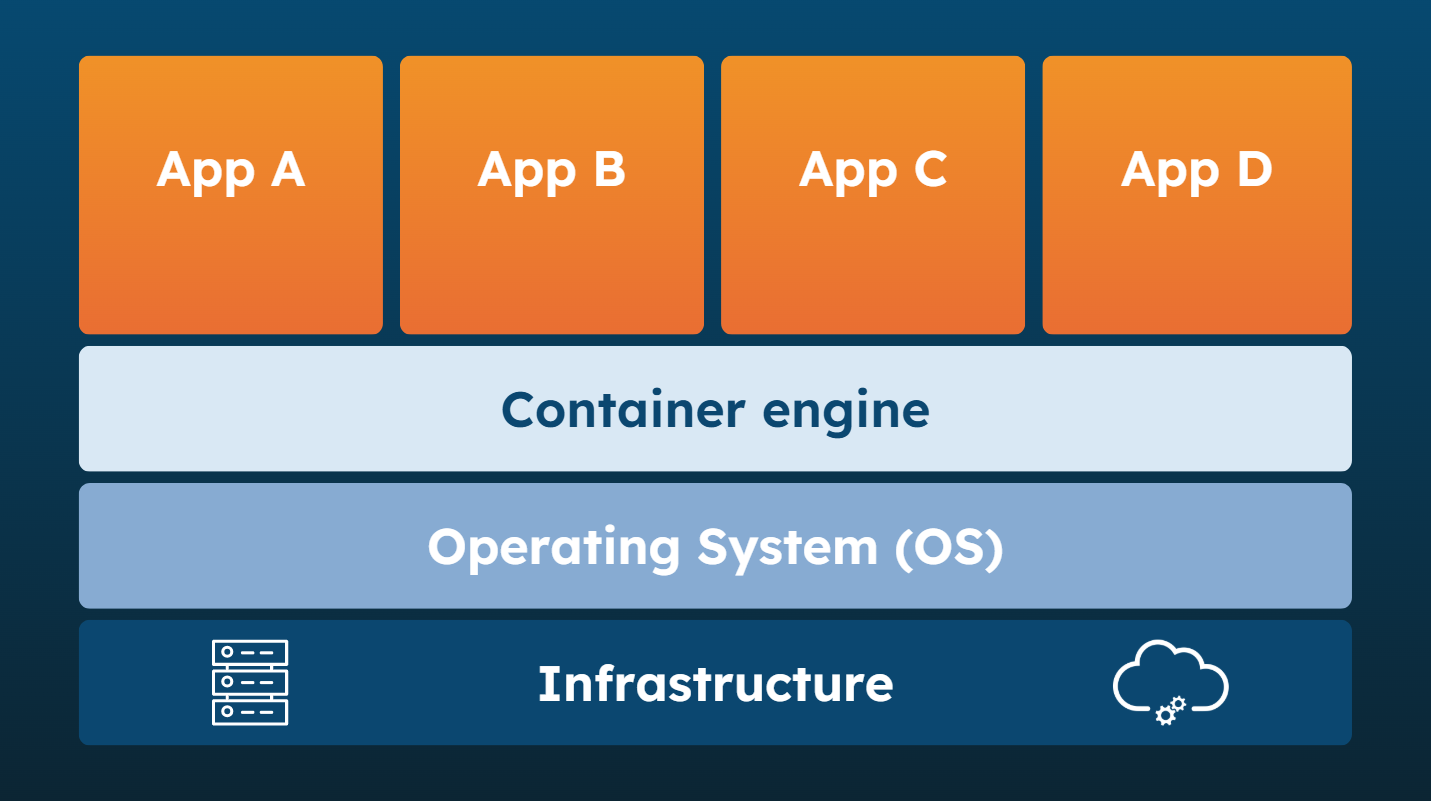
Application containerization is the practice of creating container images (similar to blueprints) of a specific segment of your system.
The images can then be started as one or multiple containers on a machine. These containers are isolated from each other, but share the OS (operating system), resulting in a more efficient usage of resources (when executed properly).
What are the benefits of application containerization?
The benefits can include, but are not limited to:
- Consistency: Containers can be created in a consistent and clean manner
- Improved efficiency: They can be (re)started up quickly, for example when there is an issue with a running container, or when responding to an increased load on the system.
- Testing: They can be tested in isolation, making for simpler testing procedures.
- Support different environments: Containers can be configured to support different environments while using the same image
- Resource management: Containers can be restricted as to how many resources they are allowed to use (CPU or memory), preventing one part of the system from negatively impacting another part of the system.
Why is application containerization important for data security?
Containerizing segments of your system as well as configuring the containers and orchestration platform properly can reduce the chances of a vulnerability being exploited. This also limits the amount of data that can be accessed or exfiltrated.
How can application containerization help with data security?
When segments of your system are separated from each other, they are only able to reach each other via the network by default. Network access can also be restricted in most container orchestration systems.
This will prevent any individually compromised system from accessing the data stored by any other system by default. Making sure that if an application is exploited, only a limited amount of data can be accessed.
Another example is that when using Linux, containers by default also have restricted OS capabilities. These can be restricted even further to prevent various security related issues, such as privilege escalation.
Conclusion
In this blog we’ve touched upon various benefits of application containerization, how it relates to data security and gave some examples of what measures can increase data security. There are many more measures that can be taken to improve data security.
To give you an idea, take a look at these resources from OWASP (Open Worldwide Application Security Project) which can be related to containerized applications: OWASP Cheat Sheet Series
These resources also give explanations as to what kind of risk you could be running if you do not follow guidelines, which can be very insightful.
If you have any questions or would like a free consultation with one of our experts, feel free to get into contact!